In an era dominated by digitalization, HTTPS phishing attacks have become a major concern for companies and individuals. The security padlock icon, representing the HTTPS protocol, is often seen as a seal of security and reliability.
However, this perception has been skillfully exploited by cybercriminals, who are using SSL certificates to mask their HTTPS phishing attacks, fooling even the most cautious users.
This article aims to debunk the myths surrounding HTTPS and offer insights into how to protect your organization against these hidden threats.
What is phishing?
Phishing is a fraudulent practice in which cybercriminals try to obtain sensitive information such as passwords, bank details and personal information by tricking victims through disguised communications.
This social engineering technique usually involves sending emails, text messages or calls that appear to be from trusted sources, such as banks, companies or even work colleagues.
Phishing attacks usuallyinduce victims to click on malicious links, download files infected with malware or provide information directly on fake websites that perfectly mimic the real ones. The growing sophistication of these scams makes it essential for Internet users to be constantly vigilant.
To protect yourself against phishing, it is crucial not to click on links in unsolicited emails or messages, especially if they ask for personal information. Always check the URL of websites before entering any data and be wary of communications that create a sense of urgency or fear.
Phishing and the security padlock
We have been taught to look for the security padlock icon when surfing the web, seeing it as a sign that a site is safe and reliable. Unfortunately, this simplistic notion has become dangerous.
The HTTPS protocol and the security padlock icon indicate that the data transmitted between the user’s browser and the web server is encrypted, making it inaccessible to malicious interceptors. However, this does not guarantee the legitimacy or “good intentions” of the site.
Obtaining an SSL certificate, which enables the HTTPS protocol, involves a Certificate Authority verifying ownership of the domain.
Even with the security lock it could be phishing
This means that while an HTTPS phishing site may not have direct access to the data entered by a user (thanks to encryption), it can still present misleading or malicious content with the appearance of being safe.
What’s more, with the increasing ease and accessibility of obtaining SSL certificates, many cybercriminals are acquiring them for their phishing sites. This allows them to display the padlock icon, exploiting the user’s trust in the symbol.
A recent survey revealed that a significant number of phishing sites now use HTTPS, making it even more difficult for ordinary users to distinguish legitimate sites from fraudulent ones based solely on the presence of the padlock.
How to identify a phishing attack?
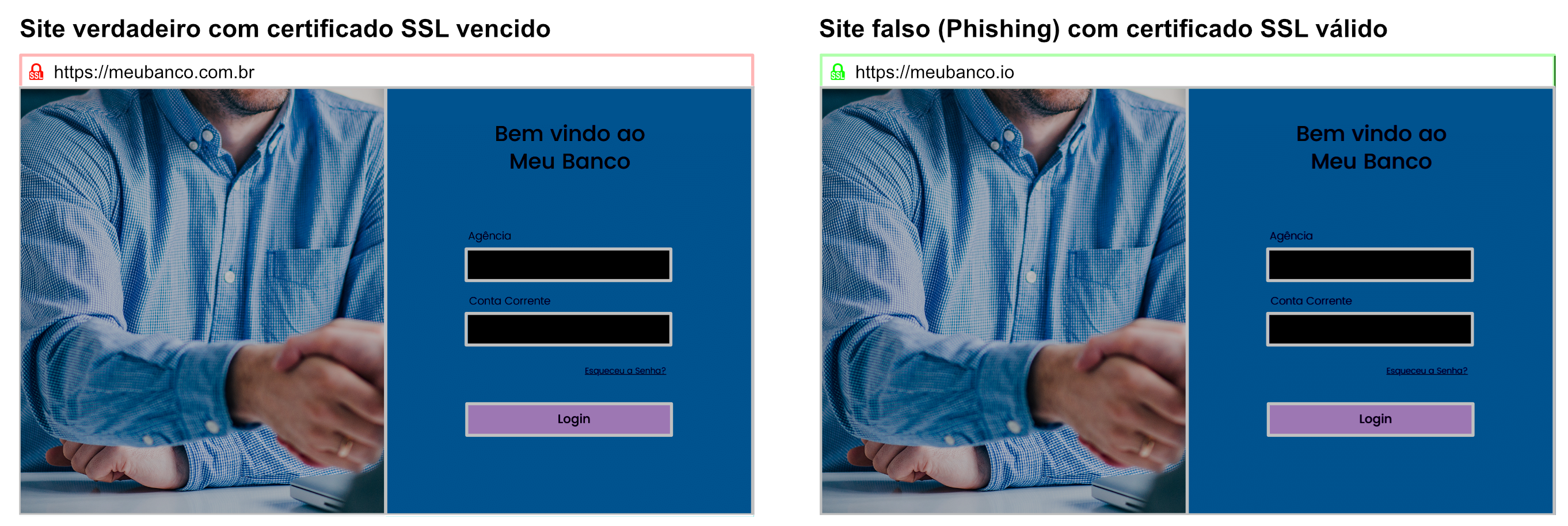
- Imagine the following situation: you receive an e-mail very similar to the one from your usual bank. In the content of the email, there is an invitation to check out the new user interface or update your account details, something simple and mundane.
- The link in the e-mail takes you to a website that looks incredibly similar to your bank’s. The resemblance is striking. The address of the bank’s original website is “meubanco.com.br”, but in this case, the address of the website to which the e-mail took you is “meubanco.io”.
The detail of the domain is subtle and most users don’t notice it.
- The site looks legitimately secure, displays the security padlock icon that you have learned to trust, located next to the URL in the browser’s address bar.
- Encouraged to proceed, you enter your branch, account number and password. The data is filled in, but an incorrect password message appears on the screen. Immediately afterwards, you are automatically redirected to the bank’s original website, “meubanco.com.br”.
- With the feeling of a simple failure, you try again, this time being careful not to get the password wrong. Access to the banking system works perfectly for this second purpose.
- However, the cybercriminal has already gained access to your bank details. During the failed attempt on the phishing site, your information was captured while you believed you were entering it on your bank’s original site.
- This alarming situation can occur with any site that requires access information, from banks to e-commerce sites.
The attacker’s objective varies according to their specific goals – be it stealing money directly through fraudulent transactions, gaining access to an account for another form of fraud or even selling these access details to third parties on the DarkWeb.
Understanding this type of attack and knowing how to identify the subtleties that give away a phishing site is essential for navigating safely in the digital age.
Always remember to check the URL, even when the site appears to be secure due to the presence of the padlock icon.
Always stay up to date and aware of the dangers online to protect your personal and financial information.
What are the types of phishing attacks?
Traditional Phishing (Email Phishing)
- Description: Involves sending emails posing as legitimate communications from well-known companies, directing victims to fake websites where they are asked for personal or financial information.
- Example: An e-mail pretending to be from your bank, asking you to confirm your account information.
Spear Phishing
- Description: A more targeted and personalized attack, where the attacker researches the victim to create a more convincing message.
- Example: An email apparently from a coworker, mentioning specific company details.
Whaling
- Description: A type of spear phishing that targets high profile or high level individuals within an organization, such as CEOs or other executives.
- Example: An email that appears to be from the company’s CFO requesting the transfer of funds to a specific account.
Vishing (Voice Phishing)
- Description: Involves the use of telephone calls to obtain personal or financial information. Attackers can usurp legitimate phone numbers to appear more trustworthy.
- Example: A call from someone pretending to be from the company’s technical support, asking to confirm network access details.
Smishing (SMS Phishing)
- Description: Uses SMS text messages to trick victims into clicking on malicious links or providing personal information.
- Example: A message saying that your account on a certain social network will be blocked unless you click on a link and confirm your information.
Clone Phishing
- Description: Involves using a legitimate email that has already been sent, but cloning it and modifying the links or attachments to malicious versions.
- Example: An e-mail that appears to be a security update from a company with which you have an account, but with links leading to a phishing site.
Pharming
- Description: Unlike other types that require the victim to click on a link, pharming redirects users from a legitimate website to a fraudulent one without them realizing it.
- Example: DNS server modifications that redirect visitors from the real banking site to an identical fake site.
CEO Fraud (Business Email Compromise – BEC)
- Description: Attackers impersonate a company executive to persuade employees to make bank transfers or disclose sensitive information.
- Example: An email pretending to be the CEO asking the finance department to make an urgent transfer.
Social Media Phishing
- Description: Using social media platforms to send misleading messages or create fake profiles in order to steal information.
- Example: A direct message on Facebook or LinkedIn asking you to click on a link to view an important document.
How to avoid phishing?
In a scenario where cybercriminals are constantly adapting their tactics, it is essential that companies stay one step ahead by implementing robust security practices.
Here are some detailed strategies that organizations can adopt to protect themselves against threats from HTTPS phishing attacks:
Continuous education and training:
The first line of defense is always the end user. Investing in regular, up-to-date training for employees can help identify and prevent phishing attempts.
Hold regular training sessions, simulating HTTPS phishing attacks to test and educate employees.
Strict verification of URLs and certificates:
Teach users to check the site URL and SSL certificate details before entering any information.
Implement tools that highlight or warn about URLs suspected of HTTPS phishing attacks and provide guides on how users can manually verify SSL certificates.
Proactive monitoring:
Keep a close eye on your company’s online presence. Actively monitoring the web for fraudulent copies of your pages can help detect and neutralize threats quickly.
Use brand and phishing monitoring services to identify fraudulent sites that imitate your brand.
Clear communication with customers:
Keep your customers informed about potential risks and what your company is doing to protect them.
Create a dedicated section on your website for security updates and send out regular communications, especially in response to known threats.
Implementation of advanced security solutions:
In addition to traditional security solutions, it is essential to adopt specific tools to manage and monitor your SSL/TLS certificates. These tools help to ensure that certificates are always up-to-date, valid and correctly configured, reducing the risk of vulnerabilities.
Solution for phishing attacks:
Eval is official Keyfactor partner
Keyfactor is a leading company in identity management and access security solutions, helping organizations around the world to protect their confidential data and guarantee the integrity of their systems.
As an official Keyfactor partner, Eval is deeply committed to assisting our clients in implementing effective security practices. Our goal is to ensure the protection of code signing keys and compliance with industry standards.
Together, we will work to offer customized and innovative solutions, taking into account the specific needs of each client.
The partnership allows us to provide an even better service to our customers, combining our experience in software security with Keyfactor’s expertise in code signing and SSL/TLS certificate management.
Contact Eval to learn more about how our partnership with Keyfactor can help you strengthen your software security and ensure the integrity of your operations.
Take advantage of the opportunity to work with Eval and Keyfactor to ensure maximum protection and efficiency in your software operations.
We are committed to providing the best security solutions to meet your specific needs and ensure the peace of mind you deserve.
About Eval
With a track record of leadership and innovation dating back to 2004, Eval not only keeps up with technological trends, but we are also in an incessant quest to bring news by offering solutions and services that make a difference to people’s lives.
With market recognized value, Eval’s solutions and services meet the highest regulatory standards for public and private organizations, such as SBIS, ITI, PCI DSS, and LGPD. In practice, we promote information security and compliance, increase companies’ operational efficiency, and reduce costs.
Innovate now, lead always: get to know Eval’s solutions and services and take your company to the next level.