Imperva stopped millions of bots from hijacking financial accounts in one of the biggest Account Takeover Attacks ever recorded.
From there, consider for a moment that an army of bots is targeting your site. They target your login page and attack it with millions of requests in a continuous attack that lasts for days.
Consequently, their infrastructure and fraud prevention costs are high. Would that scare you? What if these bots were causing problems throughout your business?
What’s more, you didn’t have the tools to block them effectively? This is the nightmare of security professionals everywhere.
Account takeover attacks by malicious bots are a real threat to your site. They can test illicitly acquired credentials in an attempt to take over users’ accounts.
This practice is known as
Credential Stuffing
. If these attempts are successful, they can inflict serious damage on your business and your brand image.
So we brought you a case of Imperva about Account Takeover Attacks. A nightmare that happened to a financial services company.
Read on to find out more.
Account Takeover Attack: Case
Imperva recently detected and mitigated the largest and longest-lasting Account Takeover (ATO) attack it has ever recorded. In this attack, the login entry point was a digital banking provider.
This resulted in more than 500 million malicious login requests over the course of three weeks, peaking at more than 25 million malicious login requests per day!
The timeline of events of the Account Takeover Attack
The campaign began on July 8, when the attackers made their first attempt to exploit the site, indicated by the short spike, colored yellow in the image below.
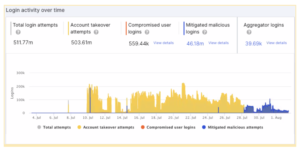
This attempt was a test to assess the target and determine whether or not it was sufficiently protected. As there was no attempt to mitigate this Account Takeover Attack, on July 10th there was a massive attack.
How do I know for sure that this is an attack?
Imperva is able to accurately determine whether requests to the login page have the characteristics of an attempted Account Takeover Attack.
However, it does this through a multi-layered process that includes reputation analysis leveraging data obtained in a collaborative manner. In other words, an advanced customer classification mechanism and proprietary algorithms developed by Imperva that include behavioral analysis models.
Therefore, Imperva’s platform approach allows us to collect data from attacks that we are seeing in our global network of clients. In addition, we use them to adjust our algorithms so that all customers benefit from them.
I can’t afford to block legitimate traffic.
Similar to the previous answer – Imperva can determine whether interactions with a site have the characteristics of an Account Takeover attempt. Precisely, which means that none of your legitimate users will be blocked.
In addition, Account Takeover protection is set up for success right after installation, ensuring that your business-critical traffic will not be affected in any way.
Will the inspection disrupt my clients’ routine?
No, our multi-layered detection approach provides focused detection with minimal false positives, reducing the need to use CAPTCHA challenges and preserving the user experience.
Will there be any additional delays?
No, Account Takeover Protection is deployed across Imperva’s global network, leveraging our robust Content Delivery Network (CDN). In this way, the company is able to deliver the best in speed, performance and endurance.
Furthermore, combined with ATO’s advanced detection, it ensures that malicious logins are mitigated immediately where they originate, long before they have a chance to reach your infrastructure.
Mitigating the attack
During the attack, Imperva’s account team worked closely with the client to alleviate any concerns. Periodically, they activated the Account Takeover mitigation to test how it affected the site.
Indicated by the blue spikes in the middle of the yellow attack traffic (in the previous image). After the account team addressed their concerns, the client fully configured the ATO mitigation.
Thus, once fully enabled, Account Takeover Attack Protection went into action immediately. And it blocked the attack traffic, which can be seen changing from yellow to blue in the graph in the previous image.
Meanwhile, legitimate users continued to log into their accounts without interruption.
About Imperva’s solution
With Imperva, you can minimize Account Takeover Attacks and prevent fraud. Imperva’s protection solution brings security to the login process, without interfering with authentic user traffic or causing delays.
This feature identifies suspicious interactions on your site, stopping potential account takeover attacks before they can threaten your infrastructure.
It also enables the analysis and detection of fraudulent activity, with a special focus on the login process. In addition, its intuitive dashboards provide visibility and useful insights into attempted attacks, user credential leaks, compromised accounts and successful logins.
In this way, the tool can identify unusual behavior that could indicate fraud in progress.
This Account Takeover Attack Protection is one of the features of Imperva’s market-leading Web & API Application Protection (WAAP).
Start protecting your Application Security today and secure your login pages.
CLICK HERE and speak to a specialist.








