Massive digitization has meant that information circulates at incredible speeds, creating global connections and interactions. However, this has also brought significant challenges in terms of cyber security. This is where technologies such as Code Signing become crucial, acting as a protective shield against various cyber threats to code signing.
The expansion of the attack surface, the growth in the sophistication of cyberattacks, and the multiplicity of threat mechanisms and channels are some of the questions that the global digital security communities are working to answer.
In fact, cybersecurity has become a crucial element in the protection of data and computerized systems as a result of these challenges. In this context, Code Signing seeks to guarantee the integrity and authenticity of the source code and protect users from malicious software.
Unraveling the Code Signing: The Technology You Can’t Ignore
Code Signing is a process that uses a cryptographic system to add a digital signature to a script or executable code.
This method is used to confirm the identity of the author of a piece of software and ensure that the code has not been altered or corrupted since it was signed. The digital signature acts as a guarantee that the software is authentic and safe to download and install.
In addition to guaranteeing the authenticity of the software, Code Signing also plays a crucial role in preventing code signing certificate theft.
In short, in the Code Signing process, the private key is used to create a digital signature, which is attached to the software.
The digital certificate, which contains the corresponding public key, is then used by users to verify the signature.
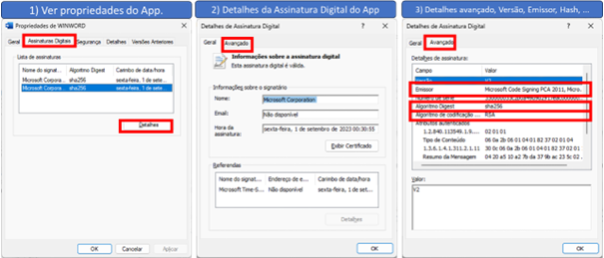
In the figure below you can see information about Word’s digital signature.
To learn more about the concepts of private key, public key, digital certificate, digital signatures, and how to protect the
code signing keys,
click here
.
The Impact of Code Signing: Maximum Protection, Minimum Risk
Code signing serves several essential purposes that benefit both developers and users.
- For developers:
Code signing helps build trust with users. When you sign your code, users know that it comes from a trusted source – see the example in figure 1, where the issuer is Microsoft, the company responsible for Word.
This can also give developers a competitive advantage, as users are more likely to download software that they know is safe and authentic, especially when they know how to protect the code signing keys.
In addition, modern operating systems generally warn or even prevent users from downloading and/or installing unsigned applications.
- For users:
Code Signing provides a guarantee of the software’s origin. By downloading digitally signed applications, users can be confident that the software really comes from the declared supplier and has not been altered by third parties.
This protects users from malware or malicious software that can be disguised as legitimate.
Code Signing on the Front Line: Combating Cyber Threats to Code Signing
Code signing protects against malware and software tampering by guaranteeing integrity verification and origin authentication. This is the time to be vigilant againstcyber threats to code signing.
Integrity check:
When code is digitally signed, any changes made to the code after signing will invalidate the digital signature.
This means that if a malicious agent tries to inject malware or otherwise tamper with the code, the digital signature will be invalid, and it will be easily noticeable.
When a user tries to install or run the software, the operating system or platform on which the software is running will check the digital signature.
If the signature is invalid, indicating that the software has been altered since it was signed, the operating system or platform may display a warning to the user or even completely block the installation or execution of the software.
Origin Authentication:
Code signing also helps to assure users that the software comes from a reliable source.
In practice, this is done by means of a Code Signing Certificate, which is linked to a specific entity (such as a company or individual developer).
The certificate is issued by a Certification Authority (CA), which verifies the identity of the entity before issuing the certificate.
In addition, when software is signed with a Code Signing Certificate, the digital signature contains information binding to the certificate. This allows users to verify the identity of the entity that signed the code.
If malicious software tries to impersonate legitimate software, it will be necessary to forge the digital signature, which is extremely difficult to do.
In summary, code signing protects against malware and software tampering by guaranteeing the integrity of signed software and providing a secure and reliable way to verify the origin of software, especially when code signing security best practices are applied.
Security Events Related to Code Signing
And as for the reality, there are several attacks that arehave become known and others are not even publicized. Below are three examples of known attacks.
1. Stuxnet:
Considered one of the most sophisticated cyber attacks ever created.
The Stuxnet malware was responsible for substantially disrupting Iran’s uranium enrichment program in 2010.
One of the most intriguing features of this malware was its ability to bypass standard security measures, as it was signed with valid certificates that had been stolen from information technology companies.
The Stuxnet case is a disturbing example that highlights the need for rigorous measures to prevent cyber threats, such as the theft of code-signing certificates.
Click here to read more about Stuxnet.
2. Flame:
An advanced malware with cyber espionage features.
The attack stood out for the way it exploited Microsoft’s code-signing infrastructure to pass itself off as a legitimate Windows component.
Using a forged certificate, this malware managed to infiltrate vulnerable systems.
Click here to see more about Flame.
3. XCode Ghost:
Incident that impacted Apple’s development environment.
Occurring in 2015, app developers downloaded a tampered version of Apple’s development environment – Xcode, which was used to inject malicious code into their apps.
When the infected apps were submitted to the App Store, they came with Apple’s official code signing certificate, so they passed legitimization.
Click here to learn more about XCode Ghost.
These examples highlight the importance of code signature security and the need to understand how to protect them to avoid similar scenarios.
This reminds us of the famous image of storing the keys under the entrance mat. There’s no point in a locked house if the keys, one of the main protection devices, are easily accessible to criminals.

The Last Line of Defense: Code Signing Security Best Practices
Although code signing is essential, it is not infallible.
In practice, the keys used in the signing process can be stolen, i.e,
protecting the keys used
is one of the weakest links today.
It is therefore crucial to adopt best practices and security policies regarding code signing to protect the keys used in the registration process.
Maintaining software reliability through secure code signing is an urgent necessity.
In addition to adopting solid IT security practices, it is equally important to focus on preventing code-signing certificate theft to ensure that the software remains secure and reliable.
About Eval
With market recognized value, Eval’s solutions and services meet the highest regulatory standards for public and private organizations, such as SBIS, ITI, PCI DSS, and LGPD. In practice, we promote information security and compliance, increase companies’ operational efficiency, and reduce costs.
Innovate now, lead always: get to know Eval’s solutions and services and take your company to the next level.
Eval, safety is value.
Article written by Marcelo Tiziano and
Evaldo.Ai
reviewed by Arnaldo Miranda.










