Have you ever wondered how software developers ensure that their applications, drivers, executables and software are authentic, complete and secure? The answer is code signing, a process that uses digital certificates and cryptography to verify the identity of the publisher and the integrity of the code.
In a nutshell, Code Signing is based on a technology called public key infrastructure (PKI), which uses public and private key pairs to create digital signatures.
The private key is used to sign the code and the public key is used to verify the signature. The public key is linked to a digital certificate that contains information about the publisher, such as name, organization and so on.
But how do publishers protect their private keys, which are Code Signing’s most important secret?
After all, if someone steals or compromises the private key, they can sign malicious code on behalf of the publisher and deceive end users.
This is where HSMs come into play in Code Signing to guarantee the security of software and applications.
The key role of HSMs in Code Signing
Code-signing attacks in recent years have been a real risk and have impacted different technology vendors, including on a recurring basis.
-
Adobe breach – 2012
Cybercriminals have breached a build server with access
Adobe’s code signing system
. Once inside, the hackers used the server to sign malware with a valid certificate.
Adobe responded by revoking the certificate, impacting three of its applications and millions of users.
-
Bit9 incident – 2013
A
Bit9 has received
reports
from its customers
that malware has been discovered on their networks – malware that has been digitally signed by Bit9’s own code-signing certificate.
It was later discovered that cybercriminals had infiltrated a virtual machine and stolen a certificate to sign and distribute the malware to at least three Bit9 clients.
-
D-Link leak – 2015
Cybercriminals don’t always need to steal a valid code signing certificate, especially when the manufacturers themselves publish it unknowingly.
In 2015,
developers at network equipment manufacturer D-Link
accidentally published four private code-signing keys in open-source firmware.
No known malware was signed with these keys, but D-Link received harsh criticism for the incident.
-
D-Link (again) – 2018
Taiwan-based technology companies D-Link and Changing Information Technology,
were targeted by another APT group known as
BlackTech
.
At least two code-signing certificates were stolen and used to sign Windows malware known as PLEAD, which steals passwords entered into the browsers of infected machines.
-
Embedded Malware – ASUS – 2019
ASUS, a well-known technology manufacturer, unknowingly,
sent malware to thousands of its customers for at least five months
.
This sophisticated attack on the software supply chain became known as “Operation ShadowHammer”.
The hackers compromised two ASUS code signing certificates and spread signed malware via the ASUS Live Update Utility, inserting backdoors into at least 1 million devices.
As more transactions, communications and operations migrate to the digital space, information security has become our greatest concern and the focus of significant advances.
That’s when HSMs (Hardware Security Modules) emerged as a robust tool for guaranteeing security in code signing.
But why are they so important? And how do they guarantee Private Key Security?
HSMs in Code Signing: Closing the Door to Threats
Code Signing is one of the main processes for maintaining the integrity and veracity of codes. In addition, it’s about establishing user trust and ensuring that codes and applications have not been altered or corrupted since their creation.
And HSMs play a crucial role in this process.
The
Hardware Security Modules
are dedicated physical devices that generate, store and protect cryptographic keys. They function as a virtual vault that facilitates secure and authentic transactions in any electronic operation, including digital code signing.
In practice, HSMs help protect the private key used in code signing from unauthorized access and the insertion of malicious code. The Key Infrastructure is the “secret” that the issuer of the signature needs to protect.
Without the protection of an HSM, private keys can be vulnerable to cyber attacks, putting the entire system at risk.
4-Step Code Signing:
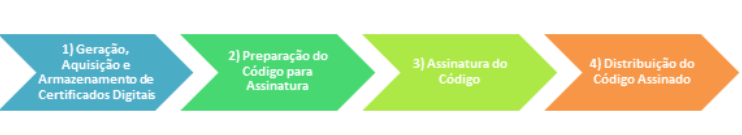
1. Generation, Acquisition and Storage of Digital Certificates:
Code signing not only involves the use of cryptographic keys, but also digital certificates, which are essential for establishing a chain of trust during the signature verification process.
Very similar to digital signatures of documents, medical certificates, contracts, among others that are widely used today.
- Generating Keys and Requesting Certificates:
First of all, you should choose a certification authority that you will be working with so that you know the process, technology and details that will be important for generating the cryptographic keys.
Knowing this, it is important to make sure that the certificate authority supports the generation of code-signing digital certificates securely within the HSM.
The normal process is to create a Certificate Signing Request (CSR), which will be sent to a Certificate Authority (CA).
- Acquisition of Digital Certificates:
Digital certificates can be purchased from a number of recognized and reliable Certificate Authorities on the market, the best known of which are
GlobalSign, DigiCert and Comodo.
- Importance of Digital Certificates:
The digital certificate contains the public key and is signed by the CA, attesting to the ownership and authenticity of the public key.
During the code signing verification process, the certificate, which is usually embedded with the application, which we’ll see later, helps to establish a chain of trust, allowing users to verify the integrity and origin of the signed code.
- Safe Storage:
Secure storage of the private keys associated with digital certificates is crucial to prevent compromise and misuse of signing credentials.
Using HSMs, private keys are stored in a highly secure environment that is resistant to extraction attempts and unauthorized access.
By ensuring that private keys are secure and that digital certificates are acquired from trusted CAs, a solid foundation is laid for a code-signing process that is both secure and reliable for end users.
2. Preparing the Code for Signing
The code that will be signed must be prepared, which usually involves compiling and packaging the software in a suitable format.
A cryptographic summary (hash) of the code is then generated, which will serve as a unique representation of the software’s content. And it’s important to pay attention at this stage, because once the hash that will be signed has been generated, there is no more room for changes to the source code.
Any bug fixes, improvements, or any other changes to the code will need to be prepared, signed off and distributed. So be careful to avoid rework.
3. Code Signing
Code signing takes place inside the HSM. The hash generated from the code is sent to the HSM, and the private key stored inside the device is used to sign this hash.
The HSM returns the digital signature, which is then attached to the software package or distributed with it.
4. Distribution of the Signed Code
Distributing signed code involves delivering the software and its digital signature to end users in a way that preserves the integrity of the signature and facilitates automatic signature verification.
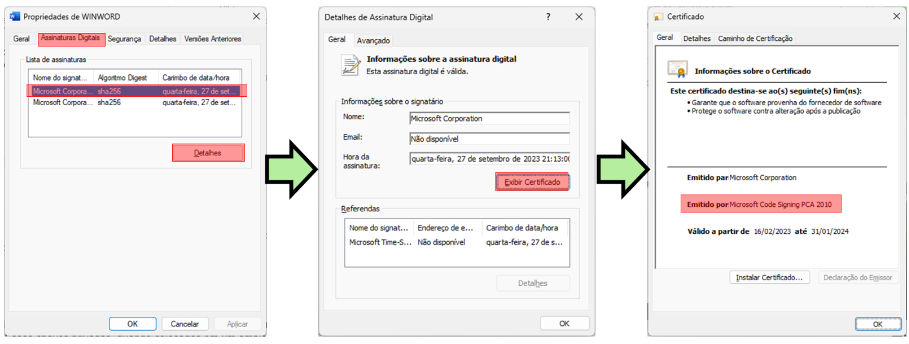
This is usually built into the application, as we can see in the case of Microsoft Word below.
Changes to the issuance of code signing certificates
The Certificate Authority/Browser (CA/B) requested that the issuance of Code Signing Certificates be changed.
These updates stipulate that a private key must be generated and protected on FIPS 140 compliant devices–2 Level 2 or Common Criteria EAL 4+ compliant devices for both Standard and EV Code Signing Certificates.
The aim is to increase the protection of the private keys associated with Code Signing Certificates and minimize the risks of malware signing using these keys.
Click here
for more information on this new determination that will be mandatory.
HSMs in Code Signing: the Key to a Secure Future
As we’ve seen in the course of this article, HSMs play a fundamental role in promoting security using Code Signing and protecting the private key.
They minimize the risks of cyber attacks, guarantee the integrity of your code and ensure confidence in your applications.
Considering our rapidly evolving digital landscape, cybersecurity isn’t just essential – it’s indispensable.
Embrace the future by committing to the security of your private key and the integrity of your code. Make HSMs your ally in the battle for impenetrable cybersecurity.
When it comes to security, there are no compromises and there can be no half-measures.
If you want to know more about how HSMs can help with code signing,
contact Eval today
and find out how we can help you protect your software and your customers.
About Eval
With a track record of leadership and innovation dating back to 2004, Eval not only keeps up with technological trends, but we are also in an incessant quest to bring news by offering solutions and services that make a difference to people’s lives.
With market recognized value, Eval’s solutions and services meet the highest regulatory standards for public and private organizations, such as SBIS, ITI, PCI DSS, and LGPD. In practice, we promote information security and compliance, increase companies’ operational efficiency, and reduce costs.
Innovate now, lead always: get to know Eval’s solutions and services and take your company to the next level.
Eval, safety is value.
Article written by Arnaldo Miranda and
Evaldo.Ai
Reviewed by Marcelo Tiziano, Design Caio Silva.










