The use of encryption and key management, as well as cryptographic services are vital for protecting data at rest or media, a reality for companies and users of services such as cloud storage, messaging and many others.
However, those responsible for these services are presented with many options for cryptographic mechanisms and consequently there are many choices to be made.
Inappropriate choices can result in little or no gain, creating a false sense of security. 
For example: encrypt a database and keep the cryptographic key in a file on the server.
In this article we intend to address some aspects relevant to information security that are related to cryptographic keys. With this we will show the importance of their correct management for the programming of cryptographic services.
To facilitate understanding, we will divide the article into three parts. Starting with the basics of cryptography, key management and cryptographic services.
Basic concepts of data encryption
Cryptography is a set of principles used to guarantee the security of information.
To do this, it uses techniques to transform one piece of information (cipher) into another (cryptogram) that is readable only by those who know the secret (secret key).
By keeping this secret safe, we prevent unauthorized persons from gaining access to the original information (decrypt).
Secrecy
The security of cryptographic services is based on the secrecy of the cryptographic key, which allows encryption and decryption, and not on the method of transforming the information, i.e. the algorithm used, which must be public.
Symmetric and asymmetric keys
In cryptography and key management there are two basic types of algorithms: symmetric and asymmetric. The former use a single key to encrypt and decrypt the data, while the latter adopt a pair of keys, one for encryption and the other for decryption.
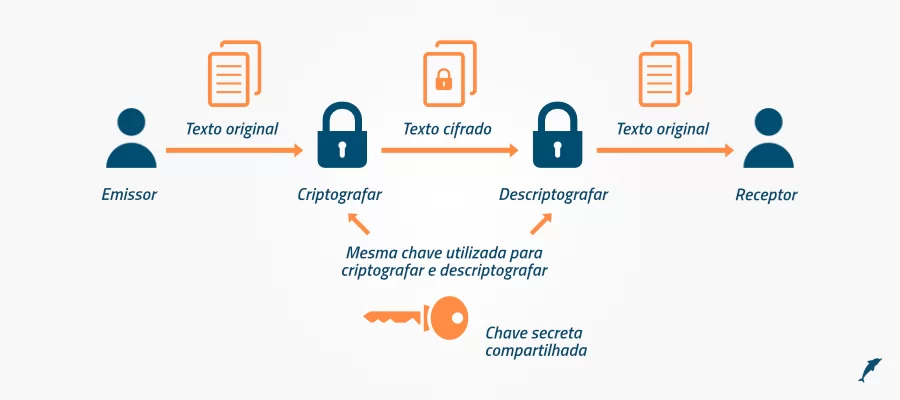
The diagram below shows the use of a symmetric key to encrypt a message. We can see that the key used by John is the same one adopted by Alice.
The next diagram shows the use of an asymmetric key. The key used by Alice to encrypt is the public key of John, who uses his private key to decrypt.
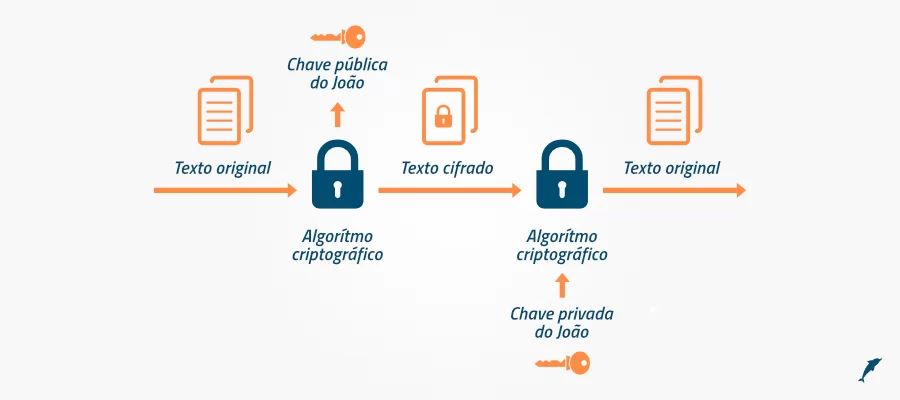
An interesting point about this type of algorithm is that after encrypting with the public key, only the private key can decrypt.
Examples of uses for these algorithms include a database that uses the AES algorithm (symmetric key) to encrypt certain information in the database and the digital signing of documents using the RSA algorithm (asymmetric key).
We would also like to point out that the secret in these two types of algorithms lies in protecting the symmetric key and the private key (in the case of asymmetric keys).
Finally, another aspect is that these algorithms are complementary and serve as the basis for programming cryptographic services.
Cryptographic summary and digital signature
In relation to cryptography and key management, a cryptographic digest is a value that represents information. It is generated using an algorithm, such as SHA256, to analyze the data bit-by-bit and creates a value that cannot be falsified in practice.

However, the cryptographic digest cannot be used on its own, because although it cannot be falsified, it can be replaced.
So, to be used in practice, the cryptographic summary is encrypted with the private key (asymmetric), generating a digital signature.
This way, everyone who has the public key can generate the cryptographic summary and compare it with the one in the digital signature.
You can then check whether the data is valid. Fundamental actions in cryptography and key management.
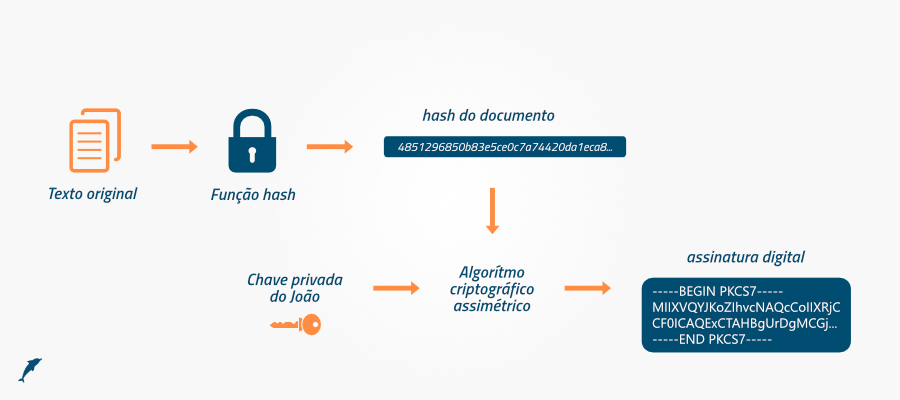
Let’s take SHA256 with RSA for example. It uses the SHA256 summarization algorithm and the RSA encryption algorithm to generate the digital signature. However, this is still not enough, as we have no way of identifying who a given public key belongs to.
This requires a new element: the digital certificate.
A digital certificate basically consists of textual information that identifies an entity (person, company or server), a public key and a purpose of use. It has a digital signature.
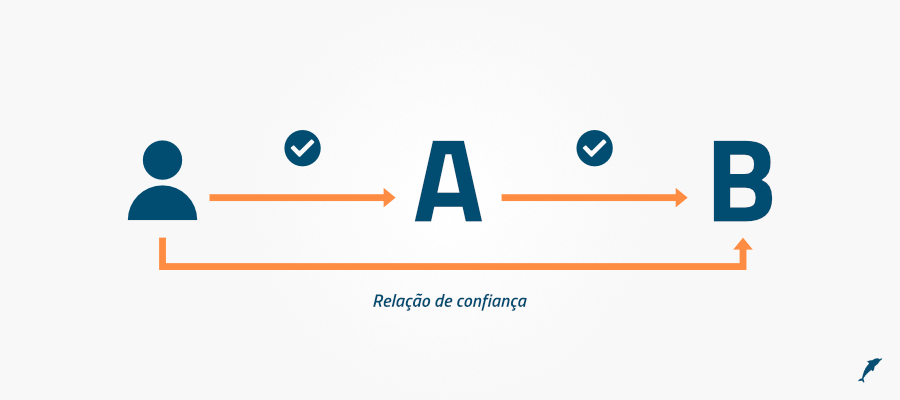
It is important to note that the digital certificate must be signed by a trusted third party (digital certification authority).
Thus, we introduced the concept of a relationship of trust. According to him, if we trust entity A and it trusts entity B, then we also trust B.
This concludes the basic concepts of cryptography. In the next part, we’ll talk about the cryptographic services that can be created from them.
Cryptographic services
As part of the cryptography and key management lifecycle, basic cryptographic mechanisms such as symmetric encryption and cryptographic digest are used to support confidentiality, integrity, authorization and irretrievability or non-repudiation services.
Thus, one cryptographic mechanism can be used to support several services. It is also important that cryptographic services should be used together to guarantee security.
Below we will briefly describe the basic cryptographic services:
Confidentiality
This service provides data confidentiality through encryption and key management. It also ensures that the information cannot be viewed by third parties and that only authorized persons have access to it. Fundamental to cryptography and key management.
Examples include encrypting files, file systems and databases with symmetric keys. We also have information encrypted with the certificate’s public key, so only those who have the corresponding private key can open the information.
Integrity
The integrity service must ensure that a given piece of information is not modified in an unauthorized way after it has been created, during transmission or storage.
Whether the change is accidental or intentional, the insertion, removal or replacement of data must be detected. Cryptographic mechanisms such as cryptographic digest, also known as hash, and digital signature provide the support for this service.
Authentication
The authentication service verifies the identity of a user or system requesting authorization to access information.
The digital signature is a cryptographic mechanism generally used to support this service, as the identification of the user has already been validated before the digital certificate is issued, either by a trusted ICP-Brasil Certificate Authority or another that the organization trusts, such as an Internal Certificate Authority.
At ICP-Brasil Certifying Authorities, it is in the process of issuing the digital certificate that the person needs to attend a face-to-face validation, with original documents proving the applicant’s identity.
|
|
Irretractability
The non-retractability service provides the means to guarantee that whoever created the information cannot deny its authenticity.
In this sense, it is linked to the digital signature, in which the owner of the private key cannot deny that he has held it for a particular purpose.
This concludes the description of cryptographic services. In the next section, we will present the main factors to be considered in key management – cryptography and key management.
Authorization
Additionally, after authentication, it is possible to use the information of the authenticated user in the system to define the authorization of the information. The authorization service provides approval or permission for the execution of an activity.
As an example, the authorization service can be employed to define the permissions to use a cryptographic key that would consequently allow access to a certain piece of information.
Cryptographic key management
Cryptographic keys are the foundation of cryptography and key management, and the security of encrypted data lies in them. Breaches can lead to compromised keys and, consequently, the leakage of sensitive information.
The increased use of encryption for data protection, mainly due to government regulations, means that companies have to deal with multiple encryption solutions.
Because of the diversity of vendors, organizations also need to define various procedures for managing cryptographic keys, and these are not always adequate.
Cryptographic key management consists of storing, protecting, organizing and ensuring the proper use of cryptographic keys, managing their lifecycle and maintaining backup copies in a secure and consistent manner.
When managing keys, we must take a few points into account, which we will describe below:
Secure storage of keys
The keys should be stored securely, i.e. encrypted and with access control.
Encryption should preferably be carried out using keys (KEK) protected on cryptographic hardware.
Identification of keys
It must be possible to identify a key, its type, its purpose, who is authorized to use it and the period of use.
User authentication and authorization
The use of cryptographic keys should only be allowed after the user has been identified.
Therefore, for proper key management, the system must provide authentication and authorization mechanisms or allow integration with existing systems, such as Microsoft’s Active Directory.
Life cycle of cryptographic keys
The lifecycle of cryptographic keys must be controlled so that they are used properly during their validity period – in other words, only authorized people or systems can use them during a predefined time and with secure mechanisms so that they are not compromised.
We will describe the life cycle of the keys, according to NIST recommendation.
The life cycle of a key starts with generation and ends with destruction, passing through one or more of the states described below:
- Generation: when the key is created and not yet ready for use;
- Pre-activation: the key has been generated, but is not yet ready for use because it is waiting for the period of use or the issue of a certificate;
- Activated: the key is available for use;
- Suspended: use of the key is temporarily suspended. In this state, it can no longer perform ciphering or signing operations, but can be used for data recovery or verification of signatures previously performed.
- Inactivated: the key can no longer be used for encryption or digital signature, but is kept for processing encrypted or signed data prior to inactivation.
- Compromised: indicates that the key has had its security affected and can no longer be used in cryptographic operations (encryption and key management). In some cases, as in symmetric keys, it can be used to recover the encrypted data for later encryption with another key.
- Destroyed: this status indicates that a key is no longer needed. The destruction of the key is the final stage and can be achieved due to the end of the key’s usage cycle or the compromise of its security.
Backing up cryptographic keys
The main function of backups is to guarantee the recovery of keys and, consequently, encrypted data in the event of loss or failure.
Just like keys, which must be stored securely during use, backup copies also need to be protected.
They can be stored in encrypted files or cryptographic hardware suitable for this purpose, which should be kept in secure locations.
About Eval
EVAL has been developing projects in the financial, health, education and industry segments for over 18 years. Since 2004, we have offered Authentication, Electronic and Digital Signature and Data Protection solutions. Currently, we are present in the main Brazilian banks, health institutions, schools and universities, and different industries.
With value recognized by the market, EVAL’s solutions and services meet the highest regulatory standards of public and private organizations, such as SBIS, ITI, PCI DSS, and the General Data Protection Law (LGPD). In practice, we promote information security and compliance, increase companies’ operational efficiency, and reduce costs.
Innovate now, lead always: get to know Eval’s solutions and services and take your company to the next level. Eval, safety is value.







