Have you ever stopped to think about how much data your company generates and stores every day? From financial information to customer data, every bit is a valuable asset that can be vulnerable to attack if not properly protected. This is where Data Encryption in Business comes in.
Data encryption in business is on the rise in the digital world due to the growing concern about assets in digital transformation projects.
These assets are distributed in the most diverse electronic environments, from local machines, servers, databases to mobile devices.
Hence the big challenge: how to protect?
O Que é Criptografia e Por Que Ela é Crucial para Seu Negócio?
Cryptography is the science and practice of protecting information by transforming it into an indecipherable code.
But why is this so important?
Imagine a world where anyone could access your financial information, business strategies or customer data.
Business Data Encryption serves as a robust shield against these threats, ensuring that only authorized people have access to critical information.
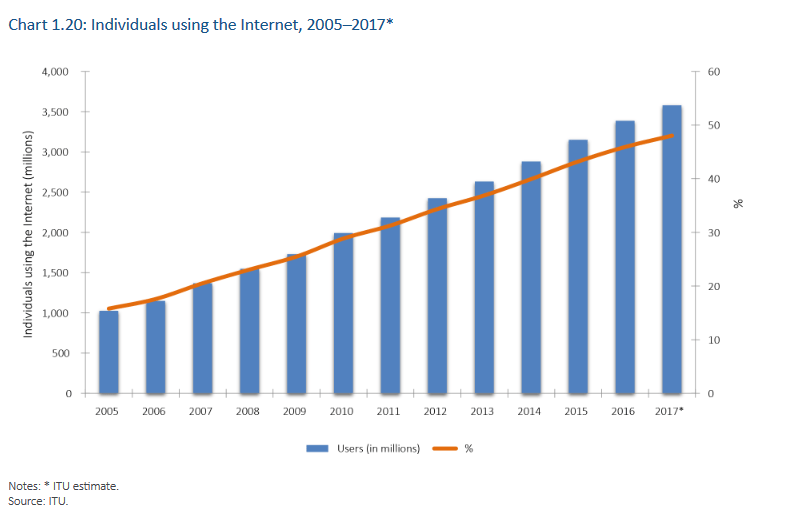
According to the ITU (International Telecommunication Union), in 2017 more than 3.6 billion people used the internet worldwide.
These people consume and generate information, so you can get an idea of the amount of data being trafficked.
Until recently, the term cryptography was unknown to most people until popular applications spread the concept.
Data encryption in business is gaining ground in the day-to-day conversations of IT professionals, from infrastructure and development to data storage.
However, due care must be taken to ensure that its benefits do not become a problem for companies.
It is known that once encrypted, the data will only be available to those who possess the secret key to decipher it.
But some doubts usually arise in this type of project, such as which data to encrypt? Will there be a loss of performance? How do I manage the keys?
Data encryption in business, should I use it?
According to the breachlevelindex website , in 2016 alone approximately 1.4 billion pieces of data were leaked. Only 4.2% of this data was encrypted, meaning that 95.8% of the data was available without any protection.
Cybercriminals are always on the prowl, looking for loopholes to break into systems and steal data. Encryption acts like a fortress wall, making it almost impossible for attackers to decipher protected information.
So you need to be one step ahead in the event of a security breach. This means putting additional protections into the organization’s strategy, such as encryption in the event of a data leak.
|
|
How Data Encryption in Business Protects You
A criptografia não é apenas uma barreira contra ameaças externas, como cibercriminosos e malware; ela também protege contra riscos internos, como funcionários descontentes ou descuidados.
Ao criptografar dados sensíveis, você garante que apenas pessoas com as credenciais corretas possam acessá-los, tornando mais difícil para qualquer parte mal-intencionada comprometer a integridade dos seus dados.
Mas os benefícios da criptografia nos negócios vai além.
Regulatory Compliance and Brand Reputation
Cumprir com regulamentações de proteção de dados não é apenas uma questão legal, mas também uma questão de reputação.
Quando os clientes sabem que você está tomando todas as medidas necessárias para proteger suas informações, a confiança na sua marca aumenta.
Isso pode se traduzir em maior fidelidade do cliente e, eventualmente, em aumento de receita.
Data Integrity and Business Continuity
A criptografia também garante que os dados não sejam alterados durante o trânsito entre diferentes sistemas ou durante o armazenamento.
Isso é crucial para a integridade dos dados e para a continuidade dos negócios, especialmente em setores como saúde e finanças, onde a precisão dos dados é imperativa.
Competitive advantage
Em um mercado saturado, ter um sistema de segurança robusto pode ser um diferencial competitivo.
Empresas que adotam medidas de segurança avançadas, como a criptografia, estão um passo à frente na atração de clientes que valorizam a privacidade e a segurança.
Implementing Technology in Business
In principle, any data can be encrypted, but it is important to define which data is sensitive for the organization. The best known are databases, file systems and virtual machines.
However, what hardly converges is the cryptographic key management model that will be used in the data protection and recovery processes.
What we’re trying to address here is: what if the key is lost?
Or what happens if the key is accessed by unauthorized users?
If these premises are not taken into account, the use of cryptographic systems, rather than a solution, becomes a major problem for an organization.
Thus, a solid solution for data encryption in business must include the adoption of a key management module that includes access control and backups.
There are several libraries that help developers with this task, as well as equipment such as HSM and Gemalto‘s KeySecure solution.
Finally, we conclude that using cryptography is a path of no return. However, projects must not overlook fundamental premises such as performance, management and secure key storage.
About Eval
A Eval está há mais de 18 anos desenvolvendo projetos nos segmentos financeiro, saúde, educação e indústria. Desde 2004, oferecemos soluções de Autenticação, Assinatura Eletrônica e Digital e Proteção de Dados. Atualmente, estamos presentes nos principais bancos brasileiros, instituições de saúde, escolas e universidades, além de diferentes indústrias.
Com valor reconhecido pelo mercado, as soluções e serviços da Eval atendem aos mais altos padrões regulatórios das organizações públicas e privadas, tais como o SBIS, ITI, PCI DSS, e a LGPD. Na prática, promovemos a segurança da informação e o compliance, o aumento da eficiência operacional das empresas, além da redução de custos.
Inove agora, lidere sempre: conheça as soluções e serviços da Eval e leve sua empresa para o próximo nível.
Eval, segurança é valor.







